Pen and Paper, Forms, QR Codes, Access Control... Which Visitor Registration Method is Right for You?
Original: https://cli.im/article/detail/2472
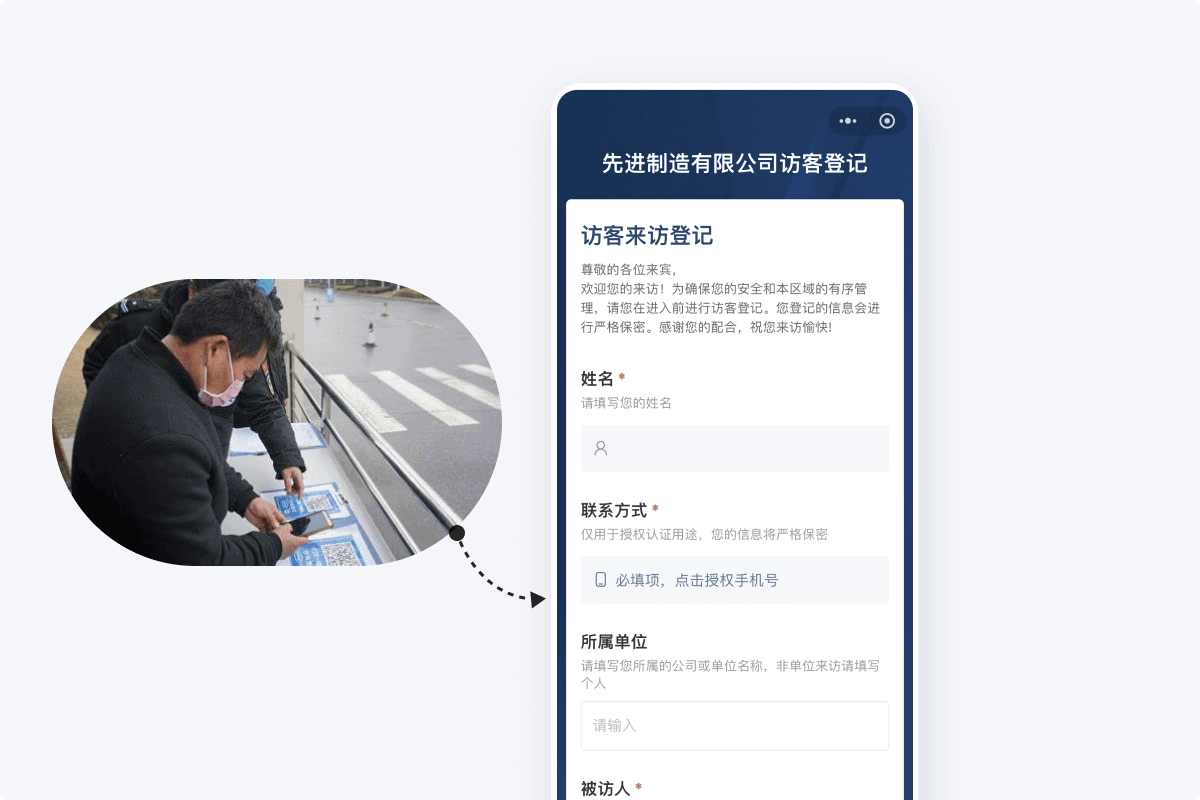
Many people consider visitor registration a mere formality: a sign-in book at the security desk where visitors jot down their name, phone number, and entry/exit times completes the process. But when items go missing, disputes arise, or inspections occur, that messy, hastily filled register often proves useless—illegible handwriting, missing information, leaving everyone in the dark.
Visitor registration is never redundant; it provides a verifiable basis for management.
1. Why Implement Visitor Registration?
1. Ensuring Safety and Traceability
The most direct function of access registration is to maintain records of personnel and vehicle movements. An unregistered visitor or an unrecorded vehicle can pose security risks. Through registration, managers can grasp the on-site situation: who entered, when, for what purpose, and who granted access.
When equipment is lost, property is damaged, or someone is injured, records help quickly identify responsible parties. With records, the sequence of events can be reconstructed, and responsibility confirmed. Without them, accountability becomes a matter of conflicting claims.
2. Compliance with Regulations and Institutional Requirements
In many industries, visitor registration is a mandatory national requirement with explicit standards, such as:
- Construction Industry: According to the "Measures for the Administration of Real-Name Registration of Construction Workers (Trial)", all construction workers must undergo real-name registration and verification before entering the site.
- Schools: For example, the "Safety Management Measures for Primary and Secondary Schools and Kindergartens" stipulate that all visitors must register and obtain a visitor pass before entering campus, to prevent unauthorized access.
- Government Agencies and Key Locations: Laws like the "Counter-Terrorism Law" require实名 registration and ID verification for personnel entering facilities, ensuring "registration upon arrival, record upon departure".
- Petroleum, Chemical, and other Hazardous Production Areas: The "Work Safety Law" and "Regulations on the Safety Management of Hazardous Chemicals" mandate that external personnel register and be issued temporary access cards before entering hazardous work zones.
The logic behind these regulations is simple: when responsibility needs defining or risks need tracing, records serve as evidence. For businesses, keeping records isn't a burden but a safeguard. In case of incidents, if regulators request data and the company cannot provide it, they bear the risk.
3. Enabling Data-Driven Management
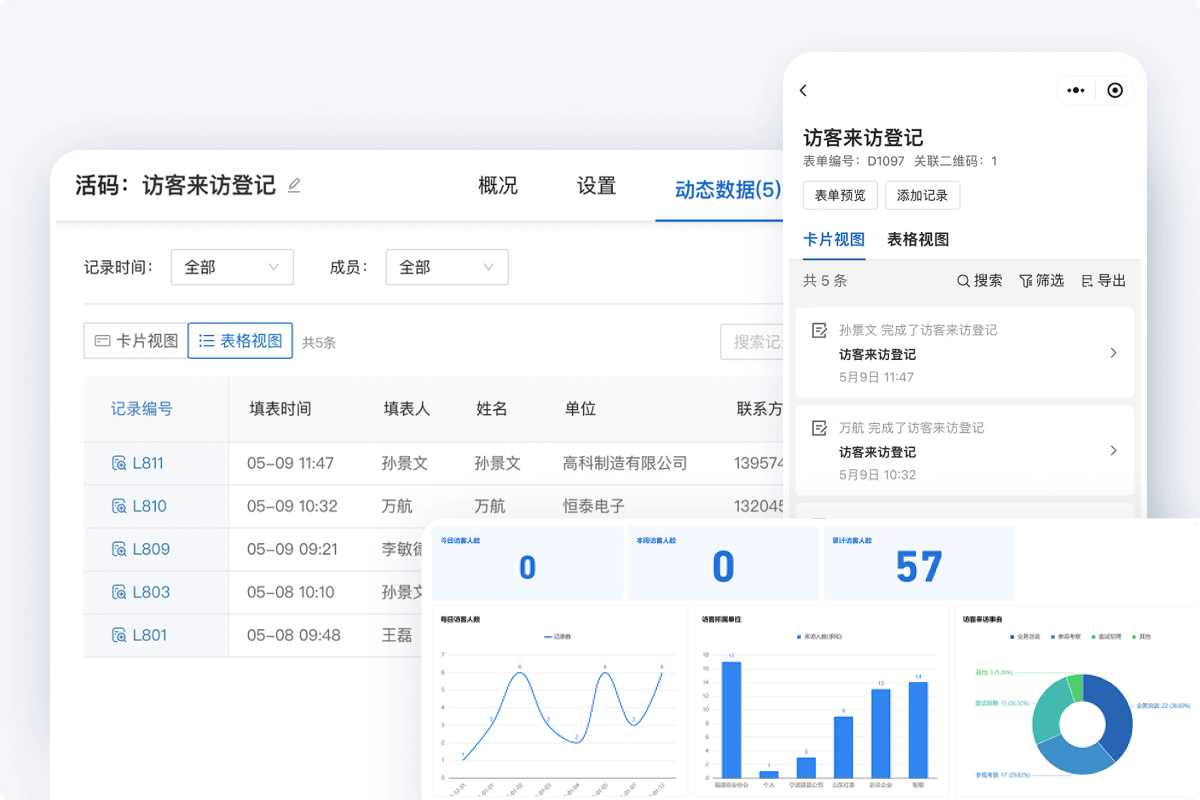
Beyond safety and compliance, visitor registration holds an often-overlooked value: data accumulation.
When registration records reach a certain volume, patterns emerge:
- How many visitors per day? Prepare materials accordingly.
- Peak traffic between 8-9 AM? Schedule an extra security guard.
- A specific supplier visits three times a week? Consider issuing a temporary pass.
This information helps managers optimize guard shifts, arrange security patrols, improve visitor reception efficiency, and even support space management and resource allocation.
An effective registration system can subtly enhance an organization's operational efficiency. This is the fundamental reason many companies are proactively adopting digital access management.
2. Comparison of Common Access Registration Methods
Current access registration methods on the market can be broadly categorized into six types, each with its pros and cons:
| Method | Description | Advantages | Disadvantages | Suitable Scenarios |
|---|---|---|---|---|
| Paper-based Registration | Handwritten name, phone, entry/exit times | Low cost, simple to use | Illegible handwriting, difficult searching, easily forged | Small guard posts, temporary projects |
| Excel Registration | Manually entered by guard post staff | Exportable, analyzable | Cumbersome operation, requires computer | Office buildings, front desk registration |
| Online Forms (e.g., Jinshan Forms) | Online filling or scan-to-fill | Quick deployment, automatic summarization | Limited application scenarios | Visitor appointments, event check-ins |
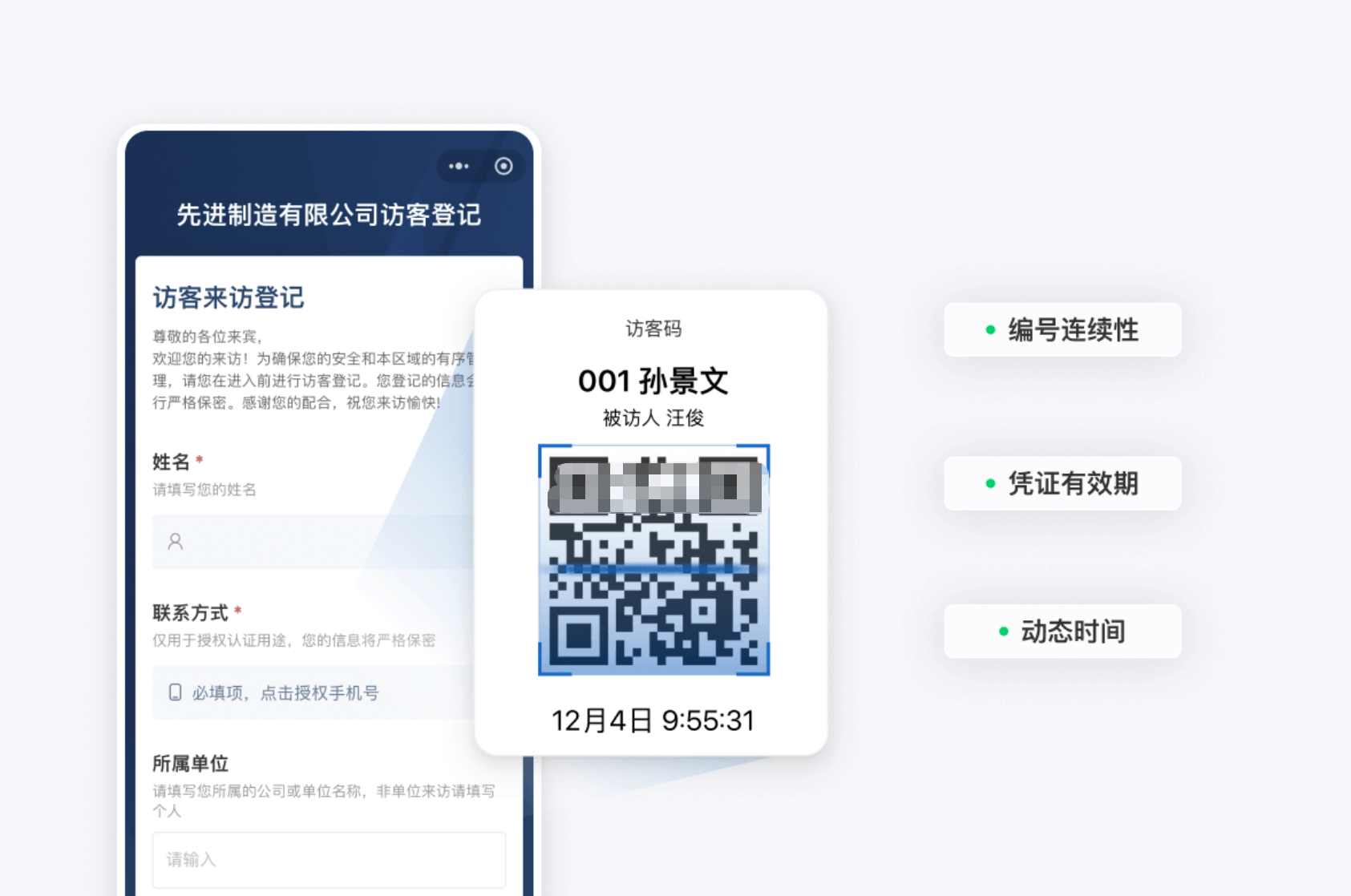
| QR Code Registration (e.g., CaoLiao QR Code) | Scan code to fill info, automatic record keeping | Flexible configuration, photo uploads possible, backend statistics | Requires internet connection | Construction sites, warehouses, properties, schools, etc. |
| OA Systems (e.g., DingTalk, WeCom) | Internal approval and visitor registration | Clear approval process, controllable permissions | Tied to organizational structure, inconvenient for external visitors | Companies already using these systems |
| Access Control / Visitor Kiosks | ID card swipe or facial recognition | High automation, strong security | High cost, complex maintenance | Government, finance, large enterprises |
3. How to Choose the Right Registration Method?
Choosing the right tool depends most critically on your company's actual situation: budget availability and visitor volume.
If you are a small or medium-sized enterprise, property management project, or construction site with limited budget and management bandwidth, a QR code registration solution is highly recommended. Using a platform like CaoLiao QR Code requires no system setup or app downloads. Just place a QR code; visitors scan to register, and complete data is automatically formed in the backend.
Registration content can be freely configured according to needs: whether to take photos, require signatures, or auto-generate timestamps is customizable. For more advanced needs, features like check-in verification, appointments, backend exports, or even API integration with access control for scan-to-open doors can be enabled.
If your organization has stricter requirements for external personnel management, such as government agencies, financial institutions, or data centers, then access control systems or visitor kiosks are more suitable, enabling deeper management like "person-certificate verification" and "behavioral record archiving".
For companies already using DingTalk or WeCom, if access registration needs are primarily internal, using their built-in visitor management modules avoids redundant deployment and facilitates permission synchronization.
Crucially, regardless of the method chosen, the registration process must not become a procedural burden nor be done merely for inspections. Otherwise, no matter how many features, if it's not executable, it's futile.
4. Doing Simple Things Well
Management improvement doesn't necessarily require expensive systems. The truly reliable solution is often not the one with the most features, but the one easiest to implement and sustain.
It might just be a QR code, a set of forms, a data platform you can understand, query, and export from.
For instance, the access registration management solution offered by CaoLiao QR Code is, for most companies, a choice that is "just sufficient, just right." It doesn't complicate the work but transforms the register from a pile of paper into queryable data.
Sometimes, what truly sets management apart isn't the sophistication of the system introduced, but who lays a more solid foundation in the basics.